With the rise of cybersecurity threats, application security is certainly getting more attention. CIOs, CISOs and other executives, responsible for implementing data protection strategies in their company, need to make sure they are protecting their corporate data, comply with the appropriate data privacy regulations such as GDPR, HIPAA, PCI and others and prevent breaches, fines and reputational damage that could seriously impact their business.

Some industry sectors, such as financial services, are increasingly being mandated to apply security patches to operating systems and desktop software to minimize any vulnerabilities.
In the first of this three-part blog series, I’ll walk you through how Quest® adheres to current software cybersecurity standards for continually testing and delivering versions of Quest Toad® products that you can safely install and run.
You’ll also see a compelling argument for staying up to date with the frequent releases of Toad products so you can avoid vulnerabilities and cybersecurity threats in the future.
Data security and Toad
First, let’s think about cybersecurity as it relates to your company’s databases, which your database administrators, developers and analysts use Toad to explore. With the growing awareness of data privacy and the rights of individuals to have their personal data protected, IT administrators are right to ask the question:

Toad products are on-premises software applications. As such, you are in full control of the data and of the security measures in place to protect it. Toad is not a hosted or SaaS solution and, therefore, does not transmit, store, access or process your data beyond its location.
Application cybersecurity and updating
Next, think about your role in keeping your network secure by continually updating your desktop software.
The ransomware attacks allowed by the WannaCry/Petya vulnerability in 2017 demonstrated that hundreds of thousands of computers worldwide were running outdated software. (Many of them probably still are.) Although the fix for WannaCry was distributed as part of a normal update to Windows, too many companies did not apply the update. Despite months of warnings, the Petya attack was a second wave against the same vulnerability, affecting computers that had not yet been updated.
Granted, some IT groups delay updates that force a system restart and interrupt productivity. Some worry about how updates will affect applications upon which thousands of their users depend. Others give priority only to necessary updates and make their own call as to what “necessary” means. Still others have an “ain’t-broke-don’t-fix-it” attitude towards software upgrades.
Many Toad customers have found themselves in that last category, asking the question,
“Toad is a fantastic product and the version we have now runs fine on hundreds of our desktops. Why should we bother to upgrade?”
In that regard, Quest is something of a victim of its own success. Although versions of Toad written years ago are still compatible with current database versions and operating systems, Quest has continually released newer, more secure versions.
Newer versions of Toad products like Toad for Oracle extend far beyond functional improvements to include substantial cybersecurity improvements. Toad’s evolution through our release process closely follows the ever-changing landscape of vulnerabilities and threats in database development, including:
- Insecure (unencrypted) connections to a database
- Unintended privilege escalation (e.g., low-privilege user to superuser)
- Incorrectly low barriers to accessing personally identifiable information (PII) and sensitive data stored in the cloud
- PII stored (and forgotten) in non-production copies of databases
Because we release new versions of Toad typically 2 – 3 times per year, you can easily upgrade to the latest version of Toad and take advantage of cybersecurity improvements that mitigate threats like these.
Update your Toad for free, with a current licenseIf you want an update/install from Quest for any Quest product, you need three things:
Your login will be tied to your Toad license. If it’s current, it will let you login to ask questions and get downloads. If you’re denied these because of maintenance issues, you’ll be contacted very soon by a Quest rep who can make sure your account information is correct or offer to update your maintenance agreement. |
Cybersecurity controls for preventing supply chain attacks
Most IT administrators are occupied with plugging security gaps among different applications installed on different platforms. That’s why Quest believes in making security practical by releasing products that are secure in the first place.
We hear about the rise of supply chain attacks, in which malware is introduced before products are released to customers. A series of scanning controls is in place to follow software cybersecurity standards for identifying and eliminating malware in the build process of Quest Toad products, including Toad for Oracle. The controls ensure that products remain free of vulnerabilities and malware, do not contain hidden backdoors and are developed by employees and contractors acting with integrity.
The table below shows the cybersecurity controls that every release of Toad undergoes.
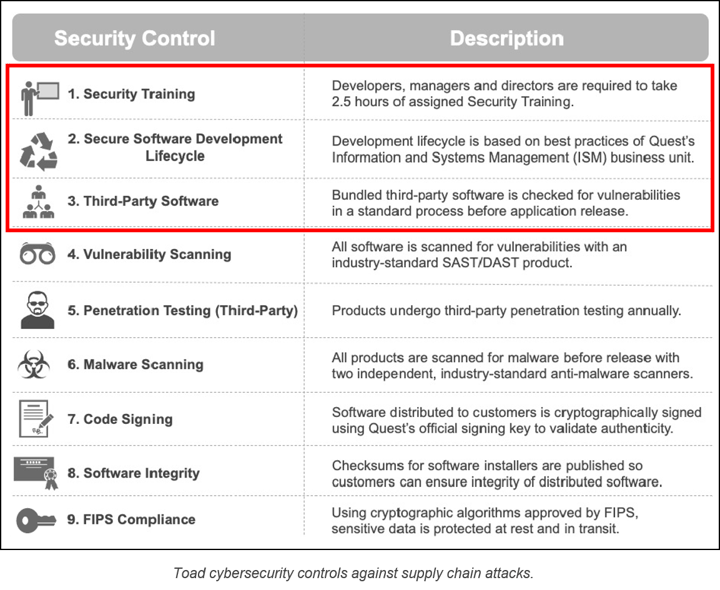
In this blog, we’re going to look at the first 3 cybersecurity controls (outlined in red above) and how Quest Software implements each of these controls for Toad products.
1. Cybersecurity training
All our software engineers, architects and managers must complete training sessions that cover the development of cybersecure software and how to write secure code. We review the training content annually to confirm it meets the requirements for developing secure software.
The goals of the training are to develop a baseline of cybersecurity knowledge, improve secure coding practices and improve adherence to the Quest Secure Software Development Lifecycle (see below). The training covers topics like understanding software cybersecurity, secure software design, secure coding, security in the Software Development Lifecycle.
2. Secure Software Development Lifecycle (SSDLC)
The SSDLC for Toad products introduces cybersecurity and privacy considerations to the process of developing the product itself. The SSDLC is designed to help Toad engineers write cybersecure software, comply with software security standards and keep engineering costs low.
The components and phases in the SSDLC include:
- Define security requirements
- Define metrics and compliance reporting
- Perform threat modeling
- Define and use cryptography standards
- Manage risk of using third-party components
- Establish a standard incident response process
3. Third-party software and component patching
Like many vendors of enterprise software, Quest often incorporates code written by other companies (“third parties”) so that Quest does not have to recreate it from scratch. But over time, vulnerabilities that require patching turn up in some third-party components.
Besides relying on the NIST CVE Database for information on current vulnerabilities, Quest uses tools to identify third-party DLLs and any vulnerabilities that may have been identified in those DLLs. Quest has also developed a process for reducing the likelihood of releasing software with vulnerable third-party components.

Next steps
In Part 2 of this blog, I’ll talk about some additional cybersecurity controls that Toad has in place for vulnerability scanning, 3rd party penetration testing and malware scanning.
For more detailed information on how Toad addresses desktop security through SSDLC, read this technical brief, “Upgrading Quest Toad for Greater Security.”
Watch the free webinar, “Why do you need to update your Toad for Oracle today?”
Try Toad for Oracle nowTry Toad for Oracle free for 30 days. Already in a trial? Talk to sales or buy now online. Already a loyal fan of Toad for Oracle? Renew now. |

Start the discussion at forums.toadworld.com