Toad for Oracle can work with MFA during the connection process to the Oracle database, if integrated through the proper Oracle client, ORA or LDAP configuration. Here’s how Toad works with different MFA and authentication methods:
Oracle Cloud Identity
Toad can connect to Oracle cloud databases that use Oracle Identity Cloud Service for MFA, which is typically via Oracle Wallet or other cloud authentication methods. See below Oracle Wallets section for additional information.
OKTA
Authentication can be done through OKTA using SSO or LDAP. If OKTA enforces MFA, Toad will prompt for that during login. Here’s how it works:
- Oracle client reads the SQLNET.AUTHENTICATION_SERVICES setting of SQLNet.ora
RADIUS Server
Authentication of Oracle databases can be configured with RADIUS for MFA. Users set up Oracle to authenticate via RADIUS, and Toad will prompt for MFA. Here’s how it works:
- Oracle client reads the SQLNET.AUTHENTICATION_SERVICES setting of SQLNet.ora
Oracle Wallets
Toad supports Oracle Wallets for secure authentication, which can be integrated with MFA when using Oracle cloud or on-premises databases.
We offer native SSL Support with or without an Oracle Client. Previously, connecting via SSL (TCPS) and using an Oracle Wallet was only possible if you had an Oracle client installed. Now, Toad supports SSL connections even without the Oracle client. Here’s how it works:
- The Oracle Wallet is configured outside of Toad.
- When using SQLNet.ora, the Oracle client reads the WALLET_LOCATION or MY_WALLET_DIRECTORY setting and applies it to all connections. Oracle Documentation
- When using TNSNames.ora, the Oracle client reads WALLET_LOCATION or MY_WALLET_DIRECTORY setting on a per-connection basis, and overrides the setting in SQLNET.Ora, if present. Oracle Documentation
- When using both files, Oracle client reads TNSNames.ora for the Wallet location
- If you’re using the Direct tab in Toad, you can specify the Wallet location by using the “more” option.
Kerberos Authentication
Toad support Kerberos authentication for secure SSO access, which can work in environments where Kerberos and MFA are enabled. Here’s how it works:
- Place KERBEROS.ini file in the same location as the TNSNames.ora
- Use “EXTERNAL” for User field and leave Password field blank
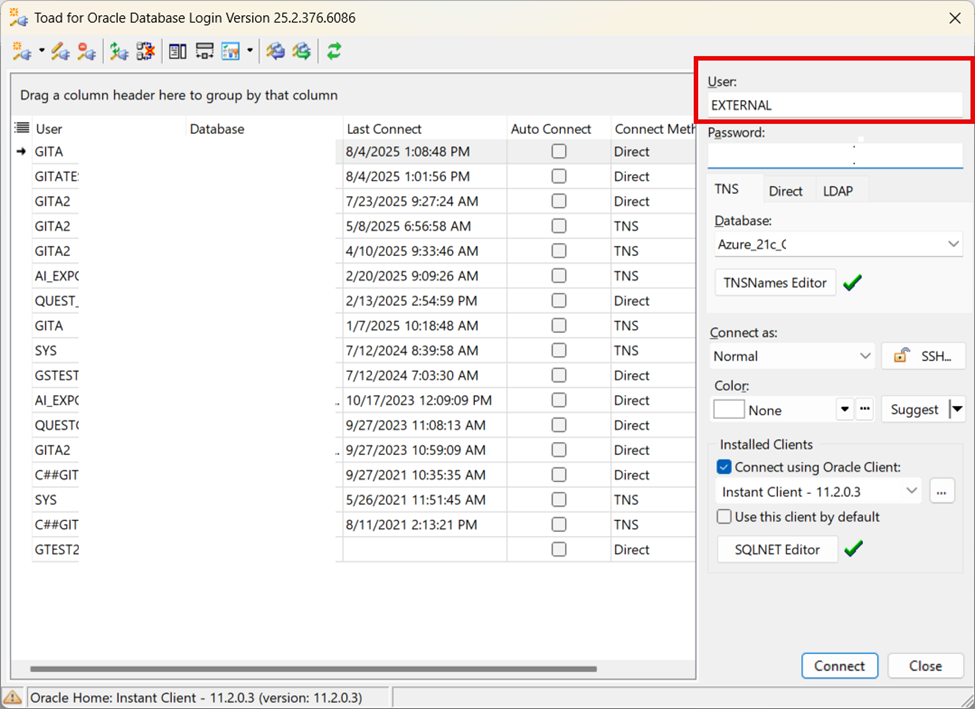
SSH Authentication
Toad can connect using SSH keys for secure (password less) authentication. Users can configure SSH authentication directly within Toad, making it easier to integrate secure connections. SSH can be combined with other MFA methods as needed.
We offer built-in SSH Tunneling without the requirement of external tools like PuTTY. Configure SSH settings in Toad by either using a private key or a password, on a per-connection basis. This works whether or not you’re using an Oracle client.
Once connected through Toad, the SSH tunnel can even be reused by other tools like SQL*Plus making it a seamless part of your development workflow. Here’s how it works:
- Use the SSH option of the Database Login window to enter required SSH parameters.
- Use Import of SSH settings window to import required parameters from PuTTY settings or other Toad connections.
Privileged Access Management (PAM)
PAM solutions such as CyberArk can randomly change account passwords as a security measure. Therefore, users need a way to pass database connection details, including credentials, without frequently entering new credentials into Toad. To accommodate this, we can utilize Toad’s support passing the database connection details including the username and password via the command line when launching the application. CyberArk has considered Toad as a supported PSM connector: CyberArk Documentation. How it works:
- Command line syntax example that can be used in PSM connector configuration:
C:\Program Files\Quest Software\Toad for Oracle 2025 R1 Edition\Toad for Oracle\toad.exe “{UserName}/{Password}@{Address}[:{Port}][/{Database}] [{ConnectAs}]”
Oracle Native Encryption and Data Integrity
Configure security features for client-server communication for encryption and data integrity check. This ensures that all connections from the client are encrypted and enforce that a checksum is established to guarantee data integrity, making certain that data hasn’t been tampered with during transmission. Toad supports the features with or without an Oracle client. Oracle Documentation
How it works using a few parameter examples:
- If SQLNET.ENCRYPTION_CLIENT=REQUIRED is set in SQLNet.ora, then the server won’t accept a connection from the client unless it is encrypted.
- If SQLNET.CRYPTO_CHECKSUM_CLIENT=REQUIRED is set in SQLNet.ora, then the server won’t accept the connection from the client unless it can establish checksum.
Support for Toad on Mac
Starting with Toad version 2025 R1, the Mac edition is shipped with an instant Oracle clients to support secure connections.
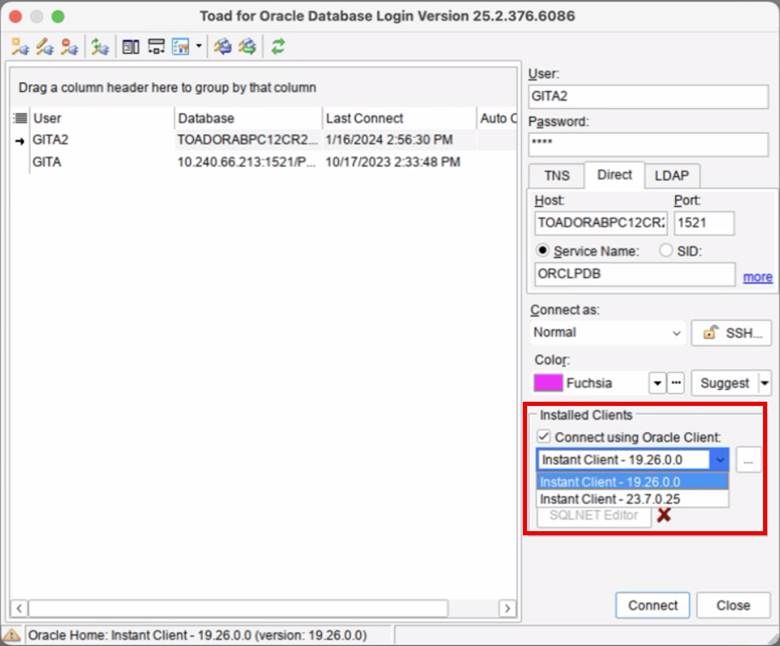
Additional enhancements in the Database Login Window
To make it easier to manage and visualize your secure connections, we’ve added a few helpful UI improvements:
- A “Secure/Insecure” status icon appears on the lower-left corner of the login window clearly showing whether an SSH connection is secure.
- A new “Lock” status icon indicates encrypted connections – planned feature for 2025 R3 release
- A new “Security” (read-only) column has been added to the login grid.
- The “Test Connections” feature now works for SSH connections.
- You can now copy SSH settings from another connection via the dropdown menu next to the SSH button.
- You can now multi-select rows, edit login records and change SSH for all selected rows at once
In summary, Toad can facilitate secure connections and work with MFA mechanisms that are configured at the Oracle database, client or network level. This gives you more flexibility to meet your organization’s security policies without extra setup overhead.
Related Links
Start the discussion at forums.toadworld.com